Java 安全架構(gòu)
注:此文章主要是sun網(wǎng)站Java安全白皮書上的一些摘要
Java
Language Security and Bytecode Verification
(Java語言安全和字節(jié)碼驗(yàn)證)
首先字節(jié)碼驗(yàn)證器檢查代碼是否滿足Java語言規(guī)范。這個(gè)任務(wù)包含兩步:(1)字節(jié)碼驗(yàn)證器分析字節(jié)碼的順序;(2)字節(jié)碼驗(yàn)證器檢查對其它類的引 用。例如�,如果一個(gè)類要訪問另一個(gè)類的方法,字節(jié)碼驗(yàn)證器就要檢查該方法是否為public。字節(jié)碼驗(yàn)證器的典型操作包括:檢查字節(jié)碼的順序是否以 0XCAFEBABE開始�,是否丟失字節(jié)�,最后的類是否包含子類(它們不應(yīng)該包括)�,方法的參數(shù)類型是什么等�。如果一切正常�,接下來類加載器將字節(jié)碼翻譯成java類,然后由java虛擬機(jī)(JVM)執(zhí)行
Basic Security Architecture(基本安全架構(gòu))
The Java platform defines a set of APIs spanning major security areas, including cryptography, public key infrastructure, authentication, secure communication, and access control. These APIs allow developers to easily integrate security into their application code. They were designed around the following principles:
1. Implementation independence(無依賴原則)
2. Implementation interoperability(相互協(xié)作原則)
3. Algorithm extensibility(算法可擴(kuò)展原則)
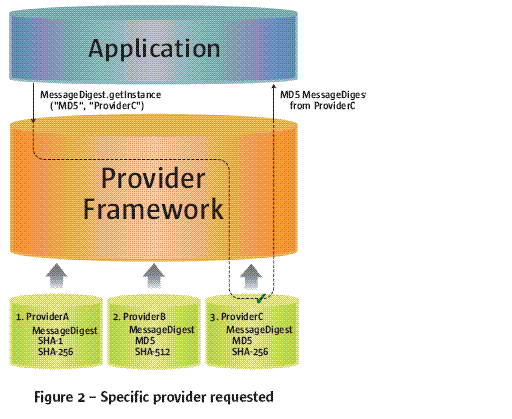
Security Providers
The java.security.Provider class encapsulates the notion of a security provider in the Java platform. It specifies the provider’s name and lists the security services it implements. Multiple providers may be configured at the same time, and are listed in order of preference. When a security service is requested, the highest priority provider that implements that service is selected.
(如果制定provider則根據(jù)制定provider來創(chuàng)建,否則默認(rèn)按照優(yōu)先級別來進(jìn)行查找)
Cryptography(密碼術(shù))
The Java cryptography architecture is a framework for accessing and developing ,
The cryptographic interfaces are provider-based, allowing for multiple and interoperable cryptography implementations. Some providers may perform cryptographic operations in software; others may perform the operations on a hardware token (for example, on a smartcard device or on a hardware cryptographic accelerator).
(允許多個(gè)實(shí)現(xiàn)一起協(xié)作�,這些providers有些可對對軟件操作,有些可對硬件操作)
cryptographic functionality for the Java platform. It includes APIs for a large variety of cryptographic services, including:
• Message digest algorithms
• Digital signature algorithms
• Symmetric bulk encryption
• Symmetric stream encryption
• Asymmetric encryption
• Password-based encryption (PBE)
• Elliptic Curve Cryptography (ECC)
• Key agreement algorithms
• Key generators
• Message Authentication Codes (MACs)
• (Pseudo-)random number generators
Public Key Infrastructure(公鑰基礎(chǔ)設(shè)施)
Public Key Infrastructure (PKI) is a term used for a framework that enables secure exchange of information based on public key cryptography. It allows identities (of people, organizations, etc.) to be bound to digital certificates and provides a means of verifying the authenticity of certificates. PKI encompasses keys, certificates, public key encryption, and trusted Certification Authorities (CAs) who generate and digitally sign certificates.
PKI Tools
There are two built-in tools for working with keys, certificates, and key stores:
keytool is used to create and manage key stores. It can
• Create public/private key pairs
• Display, import, and export X.509 v1, v2, and v3 certificates stored as files
• Create self-signed certificates
• Issue certificate (PKCS#10) requests to be sent to CAs
• Import certificate replies (obtained from the CAs sent certificate requests)
• Designate public key certificates as trusted
Authentication(認(rèn)證)
Authentication is the process of determining the identity of a user. In the context of the Java™ runtime environment, it is the process of identifying the user of an executing Java program. In certain cases, this process may rely on the services described in the “Cryptography”
Secure Communication(安全通訊)
The data that travels across a network can be accessed by someone who is not the intended recipient. When the data includes private information, such as passwords and credit card numbers, steps must be taken to make the data unintelligible to unauthorized parties. It is also important to ensure that you are sending the data to the appropriate party, and that the data has not been modified, either intentionally or unintentionally, during transport.
Cryptography forms the basis required for secure communication
The Java platform also provides API support and provider implementations for a number of standard secure communication protocols.
SSL/TLS
SASL(Simple Authentication and Security Layer)
GSS-API and Kerberos
Access Control(訪問控制)
The access control architecture in the Java platform protects access to sensitive resources (for example, local files) or sensitive application code (for example, methods in a class).
(訪問控制主要是保護(hù)一些敏感資源或者代碼�,比如本地文件或者類中的一個(gè)方法)
Permissions
Policy
Access Control Enforcement
附錄:
|
High-level Features
|
Low-level Features
|
Benefits
|
References
|
|
Platform Security
|
Built-in language security features enforced by
the Java compiler and virtual machine:
|
Provides a safe and secure platform for developing
and running applications. Compile-time data type checking and
automatic memory management leads to more robust code and reduces
memory corruption and vulnerabilities. Bytecode verification
ensures code conforms to the JVM specification and prevents
hostile code from corrupting the runtime environment. Class
loaders ensure that untrusted code cannot interfere with the
running of other Java programs.
|
|
|
Cryptography
|
-
Comprehensive
API with support for a wide range of cryptographic services
including digital signatures, message digests, ciphers
(symmetric, asymmetric, stream & block), message
authentication codes, key generators and key factories
-
Support
for a wide range of standard algorithms including RSA, DSA, AES,
Triple DES, SHA, PKCS#5, RC2, and RC4.
|
Provides an extensible, full featured API for
building secure applications:
|
|
|
Authentication and Access Control
|
-
Abstract authentication APIs that can
incorporate a wide range of login mechanisms through a pluggable
architecture.
-
A comprehensive policy and permissions API
that allows the developer to create and administer applications
requiring fine-grained access to security-sensitive resources.
|
Enables single sign-on of multiple authentication
mechanisms and fine-grained access to resources based on the
identity of the user or code signer. Recent support (in JDK
5) for timestamped signatures makes it easier to deploy signed
code by avoiding the need to re-sign code when the signer's
certificate expires.
|
|
|
Secure Communications
|
APIs and implementations for the following
standards-based secure communications protocols: Transport Layer
Security (TLS), Secure Sockets Layer (SSL), Kerberos (accessible
through GSS-API), and the Simple Authentication and Security Layer
(SASL). Full support for HTTPS over SSL/TLS is also included.
|
Authenticates peers over an untrusted
network and protects the integrity and privacy of data transmitted
between them.
|
|
|
Public Key Infrastructure (PKI)
|
Tools for managing keys and
certificates and comprehensive, abstract APIs with support for the
following features and algorithms:
-
Certificates and Certificate
Revocation Lists (CRLs): X.509
-
Certification Path Validators
and Builders: PKIX (RFC 3280), On-line Certificate Status
Protocol (OCSP)
-
KeyStores: PKCS#11, PKCS#12
-
Certificate Stores
(Repositories): LDAP, java.util.Collection
|
Eases the development and deployment of complex
PKI applications. Recent support (in JDK 5) for OCSP provides a
more scalable and timely method for applications to check
certificate revocation status.
|
|
參考資源:http://java.sun.com/developer/technicalArticles/Security/whitepaper/JS_White_Paper.pdf
http://java.sun.com/j2se/1.5.0/docs/guide/security/index.html
http://java.sun.com/javase/technologies/security/index.jsp#overview
http://www.builder.com.cn/2007/0420/388102.shtml