1、windows環境(xp\win7均可),以adminstrator登錄;
2、下載jailbreak,解包后,運行jailbreak.exe(非jailbreak.msc);
3、導出證書:Certificates - Current User > 個人 > 證書,選所有任務導出;
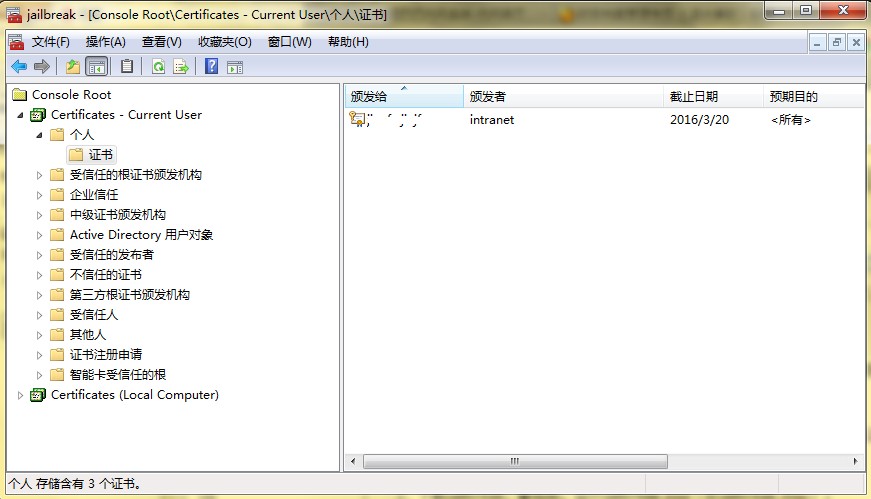
選擇導出私鑰。
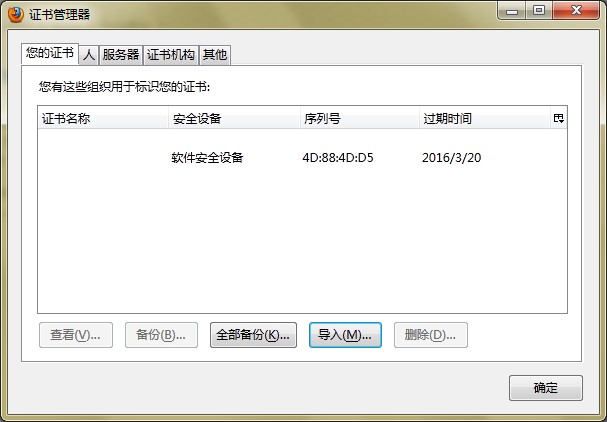
5、搞定。
]]>
過去的一年,有著太多的痛苦和艱辛,為了新產品的上線,晚上、周未都沒了,唯一想的和做的就是確保產品如期上線。過程雖然很艱苦,但大家都努力堅持,齊心協力,確保任務如期完成,我們保持了一貫的說到做到、如期交付的作風。因為這樣的磨練,我和我們的團隊得到了更多成長。困難并不可怕,熬過去,明天的太陽會更加燦爛。
1、談談成長和不足:
1)、職業轉型,開發到管理
雖然Team Leader已經做了幾年了,但一直停留在項目上,多為管事不管人,對細節問題關注較多,所以之前談不上管理,只能算是積累些項目管理經驗。經過這一年的學習和發展,有了更多的管理意識,逐漸關注團隊建設、團隊成長,注意給小組成員更多的機會和空間,讓他們得到鍛煉和成長,承擔更多團隊或項目中的重要事項,而他們通過完成這些重要任務,不僅得到了磨練,同時在團隊中建立了自己的影響力。
放在以前,我會認為有風險,或者自己做更快,更省事,或最有把握的人去。現在想來,以前認識太膚淺了,我們需要的團隊戰斗力,而不是個別人的能力,若平常不注重團隊成員的培養,團隊的戰斗力永遠不行,承擔不了關鍵任務。
談到成長和培養,團隊需要什么樣的人呢?作為互聯網企業,同一般軟件企業不同,產品在推出之前,誰也無法肯定是否會受用戶歡迎,只能快速推出,讓市場來驗證,不斷的改進和適應用戶的需要。因而,需要我們技術人員也具備技術判斷力,改變命令式管理體制下的工作習慣,充分發揮主觀能動性和創新意識,共同做好產品。
2)、學會擁抱變化;
2010年變化很多,有些也許對個人、團隊沒有影響或影響很小,有些直接關系自己或團隊,如團隊的核心成員不斷的被抽調、人員調整、KPI的271考評等,每次的變化都會帶來不同的問題。持續輸血,新人補允,使團隊戰斗力大打折扣,很長一段時間非常的糾結和無耐。事情總是具有兩面性,往好處看,這對我、對團隊也未必是件壞事,沒有經驗過挫折和磨練,又怎能成佛呢?既然是組織需要或Boss的決定,那就多些理解和支持,支持和協助上級完成也是每個下屬的職責;況且,某些變化至少對于一些同學也是件好事,他們有更多的機會和更大的平臺去一展才華。
大概人都是喜歡按習慣辦事的緣故,每每有變化都覺的很痛苦。我覺的如何擁抱變化關鍵在于心態,我們需要理性看待變化,多往積極的方向思考,不僅更容易調整好心態,而且可以在變化中吸取經驗和教訓,鞭策我們成長。
3)、提升項目管理能力
雖然在項目管理知識上沒有太多的時間和精力去系統的學習,但通過不斷實踐和總結,還是有了不少的積累和沉淀,對項目管理有了更多的理解和把握,對敏捷項目管理也有不同的認識,結合團隊自身尋找適合我們的實踐方式。在項目管理方面,還有很多需要去提升和學習,2011年希望安排更多的時間系統的學習項目管理知識及敏捷項目管理,并結合實際應用到工作中。
4)、提升向上溝通力
在擁抱變化的同時,同樣需要理性的分析和積極的向上溝通。在過去,雖然會盡可能的去表達和反饋自己的想法和意見,但我重新審視下,總覺得表達還不夠明確或不是那么的到位,或許在表達時還有更好的方式,至少還有提升的必要。向上溝通也是門學問,需要好好研究下。
5)、提升團隊建設和輔導能力
相對來說,過去的一年所有的同學都會關注到,但領悟能力和基礎較好的同學成長更快,基礎稍弱的沒有太大變化。顯然,平常輔導工作沒有做好或做到位,關注程度不夠。越是基礎差些的同學需要關注和幫助的點越多,需要幫助他們找到不足和問題所在,一起找改進辦法,并給予必要的督促和檢查,養成好的學習習慣,促進成長。2011年,這方面需要做的還有更多。
2、談談2011年的期望
1)、團隊
解決目前團隊新人多,有效資源少的問題;積極關注和幫助新人溶入團隊,熟悉業務,以減少對項目開展的影響;
抓好梯隊建設,關注和輔導基礎較差同學的,共同制定改進計劃和Action,做好必要的監督和指導,促進成長;
2)、能力
系統學習項目管理和敏捷軟件開發方面的知識,并應用到項目管理實踐中;同時積極參與相關方面的分享和討論。
3)、影響
推動興趣小組活動的開展,借開發工具的發展和分享,建立團隊在部門或技術部的影響;
鼓勵團隊成員積極參與技術部的公共事務,提升影響力。
給力2010,加油2011!!!
]]>
- 在不了解對方動機之前千萬不要表明自己的立場
- 準確把握自己的需求底線
- 解決沖突的最好辦法是談判
- 首先,以事實而后數據為依據,如果沒有,
- 以嚴密的邏輯推理為依據,如果沒有,
- 以民主評議,如果沒有,
- 以最終負責人來決斷
- 在構建獎勵制度的同時不要忘記處罰制度的建設
- 物質與非物質的獎勵(以非物質的獎勵)
- 側重獎勵行為還是結果?
表揚要及時(3天為限)、有理有據、真誠。
表揚是最不花錢最辭舊的激勵手段,表揚是為下一個成功設立起點。
不要過度的物質獎勵,在這種方式的激勵下,員工永遠得不到激勵。
要注重精神上的獎勵,只有精神是永存的。
]]>
]]>
一、相關的概念:
用戶體驗,user experience(或稱ux/ue),指用戶訪問或使用一個產品/服務時的全部感受。具有主觀性,不同的用戶本身的知識、愛好、價值觀等會有不同的結果,因人而異。
可用性,指產品是否易學、使用是否有效果,以及通用性是否良好等。衡量一個產品的可用性,可以通過一些具體目標來評判,相對用戶體驗而言,比較客觀。考察產品可用性的目標可分為:
1、可行性,指產品使用的效果;
2、有效性,產品使用的工作效率;
3、安全性,指產品能否安全的使用,或稱為容錯性;
4、通用性,指產品是否具備良好的通用性;
5、易學性,指產品的是否容易上手,易操作;
6、易記性,指產品的操作方法簡單,易記性;
二、開發人員的特點
作為一名開發者,通常會對目標用戶的判斷有較大的偏差,往往高估實際用戶的操作能力和理解能力,忽視產品的易學性和易操作性。再者,作為技術人員,開發工作者通常重視功能實現,忽視產品界面、視覺外觀,不重視用戶體驗。
三、一些案例
1、iPhone的成功
iPhone的成功,產品的可用度及用戶體驗有者至關重要的作用。其產品的很多細節,都凝聚著apple公司的創新。如3.5吋屏幕上觸摸輸入,比較費輕且易出錯,但iphone在輸入過程中,會放大選中的字符,便于用戶確認,同時,作一些輸入校驗,進行容錯處理,避免用戶輸入錯誤字符引起的麻煩。
2、在線訂票、論壇注冊
再如個在線訂票系統,用戶興沖沖的跑上來想體驗一把,千辛萬苦輸入一大段信息,終于注冊成功,想下單的時候,即發現自己有的銀行卡不支持,試想此時用戶的心情會多么的糟糕。試想一下,如果在用戶注冊前,提示系統當前支持的銀行卡的話,用戶可以第一時間選擇其他的方式來實現自己的目的。
再談論壇的會員管理機制,網上這種案例也很多。用戶費了好大的勁完成注冊后,即告知新注冊用戶不能立即發言,很可能這個用戶就這樣失去了。
所以要做好一個產品,需要每位項目成員的投入,從用戶角度出度,解決用戶的實際問題。
]]>
1、常用命令
mvn compile
編譯主程序源代碼,不會編譯test目錄的源代碼。第一次運行時,會下載相關的依賴包,可能會比較費時。
mvn test-compile
編譯測試代碼,compile之后會生成target文件夾,主程序編譯在classes下面,測試程序放在test-classes下。
mvn test
運行應用程序中的單元測試
mvn site
生成項目相關信息的網站
mvn clean
清除目標目錄中的生成結果
mvn package
依據項目生成 jar 文件,打包之前會進行編譯,測試。
mvn install
在本地 Repository 中安裝 jar。
mvn eclipse:eclipse
生成 Eclipse 項目文件及包引用定義,注意,需確保定義Classpath Variables: M2_REPO,指向本地maven類庫目錄。
2、pom.xml 說明
 <?xml version="1.0" encoding="UTF-8"?>
<?xml version="1.0" encoding="UTF-8"?> <project>
<project> <modelVersion>4.0.0</modelVersion>
<modelVersion>4.0.0</modelVersion> <groupId>com.tutorial.struts2</groupId>
<groupId>com.tutorial.struts2</groupId> <artifactId>tutorial</artifactId>
<artifactId>tutorial</artifactId> <packaging>war</packaging>
<packaging>war</packaging> <version>1.0-SNAPSHOT</version>
<version>1.0-SNAPSHOT</version> <name>Struts 2 Starter</name>
<name>Struts 2 Starter</name> <url>http://www.myComp.com</url>
<url>http://www.myComp.com</url> <description>Struts 2 Starter</description>
<description>Struts 2 Starter</description> <dependencies>
<dependencies> <!-- Junit -->
<!-- Junit --> <dependency>
<dependency> <groupId>junit</groupId>
<groupId>junit</groupId> <artifactId>junit</artifactId>
<artifactId>junit</artifactId> <version>4.4</version>
<version>4.4</version> <scope>test</scope>
<scope>test</scope> </dependency>
</dependency>
 <dependency>
<dependency> <groupId>org.springframework</groupId>
<groupId>org.springframework</groupId> <artifactId>spring</artifactId>
<artifactId>spring</artifactId> <version>2.5.5</version>
<version>2.5.5</version> </dependency>
</dependency> </dependencies>
</dependencies> </project>
</project>說明:
modelversion pom.xml 使用的對象模型版本
groupId 創建項目的組織或團體的唯一 Id
artifactId> 項目唯一Id, 項目名
packaging 打包擴展名(JAR、WAR、EAR)
version 項目版本號
name 顯示名,用于生成文檔
url 組織站點,用于生成文檔
description 項目描述,用于生成文檔
dependency之scope 管理依賴部署,取值如下:
compile 缺省值,用于所有階段,隨項目一起發布;
provided 期望JDK、容器或使用者提供此依賴。如servlet.jar;
runtime 只在運行時使用;
test 只在測試時使用,不隨項目發布;
system 需顯式提供本地jar,不在代碼倉庫中查找;
3、創建Maven Web項目
mvn archetype:generate -DgroupId=com.demo -DartifactId=web-app -DarchetypeArtifactId=maven-archetype-webapp
groupId 組織名,對應項目的package;artifactId 項目名;archetypeArtifactId 項目類型
]]>
域名綁定,包括k-system的域名及依賴環境的域名(如AEP、支付寶等)。不同的開發、測試環境只需變更k-system的變更,依賴環境的域名相同;預發環境只需綁定k-system的域名,不需依賴環境的域名綁定;生產環境則取消所有的域名綁定。基于此,一個hosts文件可分成幾個部份:與K-system無關的其他域名綁定;K-system依賴環境的域名綁定;預發環境K-system域名的綁定;開發、測試環境的K-system域名綁定。
根據上述分析,預定義若干hosts文件,分別對應上述列的幾部份內容。為每個環境建一個批處理文件,根據環境需要將這些預定義的hosts文件進行組合,并動態替換系統的hosts(C:\WINDOWS\system32\drivers\etc)文件。同時,調用IE,打開K-system登錄頁面。這樣,通過一個批處理,可以很方便的在各個環境中切換,免去經常要去編輯hosts文件的煩擾。
考慮到開發和測試會在多個本地測試環境切換,建立過多的批處理也不是個好辦法。這時,可以考慮將本地開發、測試環境的切換用同一個腳本實現,不同的環境由用戶提供運行參數來指定。如:"test_env.bat 10.2.225.87",則表示將K-system環境切換到87服務器。
部份批處理內容如下,test_env.bat:
 @echo off
@echo off
 rem 根據實際情況,修改windows的安裝目錄
rem 根據實際情況,修改windows的安裝目錄 set WIN_DIR=C:\WINDOWS
set WIN_DIR=C:\WINDOWS
 echo 生成測試hosts文件.
echo 生成測試hosts文件. if exist .env_temp del .env_temp
if exist .env_temp del .env_temp if "%1"=="" (
if "%1"=="" ( type inc\local.default >> .env_temp
type inc\local.default >> .env_temp goto endl
goto endl )
)
 echo #FI 開發、測試環境 >> .env_temp
echo #FI 開發、測試環境 >> .env_temp rem 指定其他的IP
rem 指定其他的IP echo %1 fi.alisoft.com image.alisoft.com >> .env_temp
echo %1 fi.alisoft.com image.alisoft.com >> .env_temp
 :endl
:endl
 rem 合并hosts文件
rem 合并hosts文件 call inc\merger.bat env.host inc\.env_base inc\.env_local .env_temp
call inc\merger.bat env.host inc\.env_base inc\.env_local .env_temp
 rem 備份系統的hosts
rem 備份系統的hosts set SYS_HOST=%WIN_DIR%\system32\drivers\etc\hosts
set SYS_HOST=%WIN_DIR%\system32\drivers\etc\hosts set SYS_HOST_BAK=%SYS_HOST%-bak0
set SYS_HOST_BAK=%SYS_HOST%-bak0 if not exist %SYS_HOST_BAK% (
if not exist %SYS_HOST_BAK% ( copy %SYS_HOST% %SYS_HOST_BAK%
copy %SYS_HOST% %SYS_HOST_BAK% )
)
 rem 復制hosts文件到系統目錄
rem 復制hosts文件到系統目錄 move env.host %SYS_HOST%
move env.host %SYS_HOST% del .env_temp
del .env_temp

 rem 打開瀏覽器.
rem 打開瀏覽器. call cmd /c start iexplore https://fi.alisoft.com
call cmd /c start iexplore https://fi.alisoft.com echo done!
echo done!文件合并批處理 merger.bat:
 @echo off
@echo off set output=%1
set output=%1  if exist %output% del %output%
if exist %output% del %output% :getfile
:getfile  shift
shift  if "%1"=="" goto end
if "%1"=="" goto end  type %1 >> %output%
type %1 >> %output%  goto getfile
goto getfile 
 :end
:end  set todir=
set todir= 
]]>
通過Openssl建立根證書和服務器證書,并用根證書對服務器證書進行簽名。
1、使用Openssl的CA腳本來建立根證書(/usr/share/ssl/misc/CA)
運行CA -newca,Openssl會找CA自己的私有密鑰密碼文件。如果沒有這個文件?按回車會自動創建,輸入密碼來保護這個密碼文件。之后會提示你輸入公司信息來做CA.crt文件。最后,在當前目錄下多了一個demoCA目錄,demoCA/private/cakey.pem就是CA的key文件了,而demoCA/cacert.pem就是CA的crt文件了。具體如下:
 [root@xplan-dev8 ca]# ./CA -newca
[root@xplan-dev8 ca]# ./CA -newca CA certificate filename (or enter to create)
CA certificate filename (or enter to create)
 Making CA certificate
Making CA certificate 
 Generating a 1024 bit RSA private key
Generating a 1024 bit RSA private key















 .++++++
.++++++







 ++++++
++++++ writing new private key to './demoCA/private/./cakey.pem'
writing new private key to './demoCA/private/./cakey.pem' Enter PEM pass phrase:
Enter PEM pass phrase: Verifying - Enter PEM pass phrase:
Verifying - Enter PEM pass phrase: -----
----- You are about to be asked to enter information that will be incorporated
You are about to be asked to enter information that will be incorporated into your certificate request.
into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN.
What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank
There are quite a few fields but you can leave some blank For some fields there will be a default value,
For some fields there will be a default value, If you enter '.', the field will be left blank.
If you enter '.', the field will be left blank. -----
----- Country Name (2 letter code) [GB]:CN
Country Name (2 letter code) [GB]:CN State or Province Name (full name) [Berkshire]:Zhejiang
State or Province Name (full name) [Berkshire]:Zhejiang Locality Name (eg, city) [Newbury]:Hangzhou
Locality Name (eg, city) [Newbury]:Hangzhou Organization Name (eg, company) [My Company Ltd]:Mysoft.com corpration
Organization Name (eg, company) [My Company Ltd]:Mysoft.com corpration Organizational Unit Name (eg, section) []:Mysoft.com
Organizational Unit Name (eg, section) []:Mysoft.com Common Name (eg, your name or your server's hostname) []:Mysoft.com
Common Name (eg, your name or your server's hostname) []:Mysoft.com Email Address []:
Email Address []:2、生成服務器證書
生成服務器私鑰Key文件,openssl genrsa -des3 -out server.key 1024,并輸入保護密碼:
 [root@xplan-dev8 ca]# openssl genrsa -des3 -out server.key 1024
[root@xplan-dev8 ca]# openssl genrsa -des3 -out server.key 1024 Generating RSA private key, 1024 bit long modulus
Generating RSA private key, 1024 bit long modulus ..++++++
..++++++
 ..++++++
..++++++ e is 65537 (0x10001)
e is 65537 (0x10001) Enter pass phrase for server.key:
Enter pass phrase for server.key: Verifying - Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:生成服務器證書(注:輸入Common Name一項時,若需對泛域名支持證書時,需用*.mysoft.com):
 [root@xplan-dev8 ca]# openssl req -new -key server.key -out server.csr -days 365
[root@xplan-dev8 ca]# openssl req -new -key server.key -out server.csr -days 365 Enter pass phrase for server.key:
Enter pass phrase for server.key: You are about to be asked to enter information that will be incorporated
You are about to be asked to enter information that will be incorporated into your certificate request.
into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN.
What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank
There are quite a few fields but you can leave some blank For some fields there will be a default value,
For some fields there will be a default value, If you enter '.', the field will be left blank.
If you enter '.', the field will be left blank. -----
----- Country Name (2 letter code) [GB]:CN
Country Name (2 letter code) [GB]:CN State or Province Name (full name) [Berkshire]:Zhejiang
State or Province Name (full name) [Berkshire]:Zhejiang Locality Name (eg, city) [Newbury]:Hangzhou
Locality Name (eg, city) [Newbury]:Hangzhou Organization Name (eg, company) [My Company Ltd]:Mysoft.com
Organization Name (eg, company) [My Company Ltd]:Mysoft.com Organizational Unit Name (eg, section) []:Mysoft.com
Organizational Unit Name (eg, section) []:Mysoft.com Common Name (eg, your name or your server's hostname) []:*.mysoft.com
Common Name (eg, your name or your server's hostname) []:*.mysoft.com Email Address []:
Email Address []:
 Please enter the following 'extra' attributes
Please enter the following 'extra' attributes to be sent with your certificate request
to be sent with your certificate request A challenge password []:
A challenge password []: An optional company name []:
An optional company name []:3、用根證書對服務器證書進行簽名
把server.crt文件重命名成newreq.pem,然后用CA腳本進行簽名,期間會提示要求輸入cakey.pem的保護密碼。
[root@xplan-dev8 ca]# ./CA -sign
Using configuration from /usr/share/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Dec 8 12:27:14 2008 GMT
Not After : Dec 8 12:27:14 2009 GMT
Subject:
countryName = CN
stateOrProvinceName = Zhejiang
localityName = Hangzhou
organizationName = Mysoft.com
organizationalUnitName = Mysoft.com
commonName = *.mysoft.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
0F:0C:46:82:EB:68:61:CE:6F:06:10:78:BC:7B:2F:10:F8:96:7E:09
X509v3 Authority Key Identifier:
keyid:E0:01:2C:50:62:87:8D:10:7A:17:6D:AB:2C:43:0A:79:EB:5F:26:0C
DirName:/C=CN/ST=Zhejiang/L=Hangzhou/O=Mysoft.com corpration/OU=Mysoft.com/CN=Mysoft.com
serial:00
Certificate is to be certified until Dec 8 12:27:14 2009 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: md5WithRSAEncryption
Issuer: C=CN, ST=Zhejiang, L=Hangzhou, O=Mysoft.com corpration, OU=Mysoft.com, CN=Mysoft.com
Validity
Not Before: Dec 8 12:27:14 2008 GMT
Not After : Dec 8 12:27:14 2009 GMT
Subject: C=CN, ST=Zhejiang, L=Hangzhou, O=Mysoft.com, OU=Mysoft.com, CN=*.mysoft.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:f0:46:a7:a3:9d:8d:ce:09:da:f1:02:a0:fd:1f:
5c:df:a5:08:66:ea:13:0d:17:ac:49:92:9f:65:21:
cf:ec:f8:79:73:a1:73:0a:3e:d6:d0:c3:a4:d4:36:
22:b8:4c:82:51:fe:5d:e1:13:22:99:5f:4c:ef:c6:
65:3a:5d:de:1f:83:f2:17:a5:2b:f3:03:94:9a:31:
bc:09:c8:1c:9e:4d:ad:3b:90:2d:dc:65:0c:e3:04:
9b:8a:d5:c2:93:b7:51:8e:fe:92:1d:ee:55:6e:a0:
77:25:e1:a1:24:7f:55:7a:b4:4d:f4:84:83:13:56:
8d:62:be:2d:db:f8:1a:de:35
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
0F:0C:46:82:EB:68:61:CE:6F:06:10:78:BC:7B:2F:10:F8:96:7E:09
X509v3 Authority Key Identifier:
keyid:E0:01:2C:50:62:87:8D:10:7A:17:6D:AB:2C:43:0A:79:EB:5F:26:0C
DirName:/C=CN/ST=Zhejiang/L=Hangzhou/O=Mysoft.com corpration/OU=Mysoft.com/CN=Mysoft.com
serial:00
Signature Algorithm: md5WithRSAEncryption
0b:dc:15:f3:87:5c:e0:07:23:0e:78:47:af:56:fb:43:31:4b:
0d:12:76:57:95:cd:d7:2a:75:00:01:21:96:9d:d4:bf:9d:e9:
b6:26:cc:70:98:95:fd:ca:af:ad:68:fb:10:79:09:05:32:20:
02:7a:84:53:2f:e0:d5:cd:ed:4d:42:e7:d5:9d:90:78:9a:2e:
d8:72:cb:7f:f7:29:30:24:25:f2:0f:2d:b4:9d:a2:b3:24:00:
b4:f7:e9:de:5c:1a:50:d3:59:a4:9c:1d:03:15:04:17:6d:c2:
ab:95:a8:1f:28:e5:ad:3c:a9:a8:c8:30:3a:09:3f:75:5d:70:
2e:af
-----BEGIN CERTIFICATE-----
MIIDfDCCAuWgAwIBAgIBATANBgkqhkiG9w0BAQQFADCBgDELMAkGA1UEBhMCQ04x
ETAPBgNVBAgTCFpoZWppYW5nMREwDwYDVQQHEwhIYW5nemhvdTEfMB0GA1UEChMW
QWxpc29mdC5jb20gY29ycHJhdGlvbjEUMBIGA1UECxMLQWxpc29mdC5jb20xFDAS
BgNVBAMTC0FsaXNvZnQuY29tMB4XDTA4MTIwODEyMjcxNFoXDTA5MTIwODEyMjcx
NFowdzELMAkGA1UEBhMCQ04xETAPBgNVBAgTCFpoZWppYW5nMREwDwYDVQQHEwhI
YW5nemhvdTEUMBIGA1UEChMLQWxpc29mdC5jb20xFDASBgNVBAsTC0FsaXNvZnQu
Y29tMRYwFAYDVQQDFA0qLmFsaXNvZnQuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GN
ADCBiQKBgQDwRqejnY3OCdrxAqD9H1zfpQhm6hMNF6xJkp9lIc/s+HlzoXMKPtbQ
w6TUNiK4TIJR/l3hEyKZX0zvxmU6Xd4fg/IXpSvzA5SaMbwJyByeTa07kC3cZQzj
BJuK1cKTt1GO/pId7lVuoHcl4aEkf1V6tE30hIMTVo1ivi3b+BreNQIDAQABo4IB
DDCCAQgwCQYDVR0TBAIwADAsBglghkgBhvhCAQ0EHxYdT3BlblNTTCBHZW5lcmF0
ZWQgQ2VydGlmaWNhdGUwHQYDVR0OBBYEFA8MRoLraGHObwYQeLx7LxD4ln4JMIGt
BgNVHSMEgaUwgaKAFOABLFBih40QehdtqyxDCnnrXyYMoYGGpIGDMIGAMQswCQYD
VQQGEwJDTjERMA8GA1UECBMIWmhlamlhbmcxETAPBgNVBAcTCEhhbmd6aG91MR8w
HQYDVQQKExZBbGlzb2Z0LmNvbSBjb3JwcmF0aW9uMRQwEgYDVQQLEwtBbGlzb2Z0
LmNvbTEUMBIGA1UEAxMLQWxpc29mdC5jb22CAQAwDQYJKoZIhvcNAQEEBQADgYEA
C9wV84dc4AcjDnhHr1b7QzFLDRJ2V5XN1yp1AAEhlp3Uv53ptibMcJiV/cqvrWj7
EHkJBTIgAnqEUy/g1c3tTULn1Z2QeJou2HLLf/cpMCQl8g8ttJ2isyQAtPfp3lwa
UNNZpJwdAxUEF23Cq5WoHyjlrTypqMgwOgk/dV1wLq8=
-----END CERTIFICATE-----
Signed certificate is in newcert.pem
這樣就生成了server的證書newcert.pem,把newcert.pem 重命名為server.crt。
4、配置apache

 NameVirtualHost *:443
NameVirtualHost *:443 <VirtualHost *:443>
<VirtualHost *:443> ServerAdmin sa@mysoft.com
ServerAdmin sa@mysoft.com ServerName xplan.mysoft.com
ServerName xplan.mysoft.com DocumentRoot /home/admin/project/htdocs
DocumentRoot /home/admin/project/htdocs
 SSLEngine on
SSLEngine on SSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+SSLv3:+EXP:+eNULL
SSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+SSLv3:+EXP:+eNULL SSLCertificateFile /home/admin/modules/crt/server.crt
SSLCertificateFile /home/admin/modules/crt/server.crt SSLCertificateKeyFile /home/admin/modules/crt/server.key
SSLCertificateKeyFile /home/admin/modules/crt/server.key
 SSLProxyEngine on
SSLProxyEngine on RewriteEngine on
RewriteEngine on RewriteRule ^/$ /xplan/user/login!login.jspa [L,P]
RewriteRule ^/$ /xplan/user/login!login.jspa [L,P] </VirtualHost>
</VirtualHost>重啟apache時,會提示要求輸入服務端證書的密碼。如下:
 [root@localhost]# bin/apachectl restart
[root@localhost]# bin/apachectl restart httpd not running, trying to start
httpd not running, trying to start Apache/2.2.0 mod_ssl/2.2.0 (Pass Phrase Dialog)
Apache/2.2.0 mod_ssl/2.2.0 (Pass Phrase Dialog) Some of your private key files are encrypted for security reasons.
Some of your private key files are encrypted for security reasons. In order to read them you have to provide the pass phrases.
In order to read them you have to provide the pass phrases.
 Server xplan.mysoft.com:443 (RSA)
Server xplan.mysoft.com:443 (RSA) Enter pass phrase:
Enter pass phrase:
 OK: Pass Phrase Dialog successful.
OK: Pass Phrase Dialog successful.
5、客戶端(IE)導入根證書(ca.cert)
在"選項"->"內容"->"證書"->"受信任根證書頒發機構"中點擊"導入",選中"ca.crt",完成導入。或者,直接在點ca.crt文件右鍵,選擇安裝即可。
6、重啟apache,要求輸入密碼的問題解決
1)、去掉bin/apachectl start啟動的pass phrase,用空pass phrase啟動apache
(while preserving the original file):
[root@xplan-dev8 ca]$ cp server.key server.key.org
[root@xplan-dev8 ca]$ openssl rsa -in server.key.org -out server.key
確認server.key 文件為root可讀
[root@xplan-dev8 ca]$ chmod 400 server.key
2、編輯
[root@xplan-dev8 ca]$ vi conf/extra/httpd-ssl.conf
注釋SSLPassPhraseDialog builtin
在后添加:SSLPassPhraseDialog exec:/usr/local/apache2/conf/apache_pass.sh
[root@xplan-dev8 ca]$ vi conf/apache_pass.sh
#!/bin/sh
echo "密碼"
[root@xplan-dev8 ca]$ chmod +x /usr/local/apache2/conf/apache_pass.sh
]]>

]]>
Apache 下載(包含OpenSSL的版本): http://httpd.apache.org/download.cgi
Apache與Tomcat的連接器: jakarta-tomcat-connectors-jk2.0.4-win32-apachex.x.xx.zip
二、Apache 配置
安裝過程很簡單,按默認安裝即可。Apache配置文件conf/httpd.conf 需要做的修改如下:
Listen 443
ServerName crm.company.com
#確認下列module啟用
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_connect_module modules/mod_proxy_connect.so
LoadModule proxy_http_module modules/mod_proxy_http.so
LoadModule rewrite_module modules/mod_rewrite.so
LoadModule ssl_module modules/mod_ssl.so
#需將默認的SSL配置注釋(也可將下面虛擬機中關于SSL的配置更改到ssl.conf)
#<IfModule mod_ssl.c>
# Include conf/ssl.conf
#</IfModule>
#定義虛擬主機
NameVirtualHost *:443
<VirtualHost *:443>
ServerAdmin admin@company.com
ServerName crm.company.com
DocumentRoot E:/projects/crm/htdocs
SSLEngine On
SSLCipherSuite ALL:!ADH:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+SSLv3:+EXP:+eNULL
SSLCertificateFile D:/Services/crt/crm.crt
SSLCertificateKeyFile D:/Services/crt/crm.key
SSLProxyEngine on
RewriteEngine on
RewriteRule ^/$ /crm/login!login.jspa [L,P]
</VirtualHost>
三、Jboss 配置
解壓后即完成安裝,應用配置需要修改的配置文件為:server\default\conf\jboss-service.xml
<attribute name="URLs">
deploy/, file:/d:/project/crm/deploy/target/
</attribute>
四、Apache 與 Jboss集成
1、將mod_jk2.so文件拷貝到Apache安裝目錄下的modules文件夾中,并修改Apache的配置文件(httpd.conf),加入如下內容:
<IfModule mod_jk2.c>
JkSet config.file ./workers2.properties
</IfModule>
LoadModule jk2_module modules/mod_jk2.so
2、在Apache配置目錄conf下新建文件work.properties,并加入如內容:
port=8009
host=127.0.0.1
[ajp13:localhost:8009]
channel=channel.socket:localhost:8009
[uri:/*]
[uri:/*.jsp]
[uri:/*.jspa]
worker=ajp13:localhost:8009
3、JBOSS的server\default\conf目錄下,新建一個jk2.properties的文件,內容如下:
handler.list=apr,request,channelSocket
#
# Override the default port for the socketChannel
channelSocket.port=8009
五、測試
完成上述配置后,分別啟動Jboss和Apache,使用https訪問應用,如https://crm.company.com,apache收到請求后,按虛擬機中設置的kURL重寫規則,轉向/crm/login!login.jspa。連接器檢測到jspa文件,則將該請求轉給Jboss處理。如jspa頁面的內容被顯示出來,則表示配置成功。
六、小結
配置過程中,httpd.con配置比較容易出現問題,一般使用apache提供的配置文件檢測功能,確定httpd.conf正確。其次,可查看apache的log日志文件,按日志文件的錯誤描述進行處理。
配置過程中,可按步進行:Apache & ssl配置;Jboss 應用配置;集成配置;如此可減少一些問題。
]]>
 @echo off
@echo off title 刪除 Windows Genuine Advantage 腳本
title 刪除 Windows Genuine Advantage 腳本 cls
cls :ClearTemp
:ClearTemp echo.
echo. echo.
echo. set choice=
set choice= set /p choice= 是否要嘗試刪除 Windows Genuine Advantage (Y/N)?:
set /p choice= 是否要嘗試刪除 Windows Genuine Advantage (Y/N)?: if "%choice%"=="N" goto End
if "%choice%"=="N" goto End if "%choice%"=="n" goto End
if "%choice%"=="n" goto End echo.
echo. echo 正在嘗試刪除 Windows Genuine Advantage ……
echo 正在嘗試刪除 Windows Genuine Advantage …… echo.
echo. taskkill /f /im wgatray.exe /t
taskkill /f /im wgatray.exe /t taskkill /f /im wgatray.dll /t
taskkill /f /im wgatray.dll /t del /f /q %systemroot%\system32\wga*.*
del /f /q %systemroot%\system32\wga*.* taskkill /f /im wgatray.exe /t
taskkill /f /im wgatray.exe /t taskkill /f /im wgatray.dll /t
taskkill /f /im wgatray.dll /t del /f /q %systemroot%\system32\wga*.*
del /f /q %systemroot%\system32\wga*.* taskkill /f /im wgatray.exe /t
taskkill /f /im wgatray.exe /t taskkill /f /im wgatray.dll /t
taskkill /f /im wgatray.dll /t del /f /q %systemroot%\system32\wga*.*
del /f /q %systemroot%\system32\wga*.* taskkill /f /im wgatray.exe /t
taskkill /f /im wgatray.exe /t taskkill /f /im wgatray.dll /t
taskkill /f /im wgatray.dll /t del /f /q %systemroot%\system32\wga*.*
del /f /q %systemroot%\system32\wga*.*
 del /f /q %systemroot%\system32\legitcheckcontrol.dll
del /f /q %systemroot%\system32\legitcheckcontrol.dll del /f /q %systemroot%\system32\dllcache\wga*.*
del /f /q %systemroot%\system32\dllcache\wga*.*
 reg delete HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\WGALogon /f
reg delete HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify\WGALogon /f reg delete HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\uninstall\wganotify /f
reg delete HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\uninstall\wganotify /f
 :End
:End echo.
echo. echo -----------------------處理完畢。請關閉。-----------------------
echo -----------------------處理完畢。請關閉。----------------------- echo.
echo. echo.
echo. pause>nul
pause>nul
]]>
netsh interface ip add dns name = "本地連接" addr = 202.101.172.35
netsh interface ip add dns name = "本地連接" addr = 202.101.172.36
]]>
無良人類總是不斷的制造出新病毒和流氓軟件,從中獲取利益,強烈的鄙視這群人!!
可憐我的Norton能殺,但不能清理干凈,郁悶至極!找了個金山毒霸的專殺工具,在windows下殺出了一個kson.exe!!
希望問題已經解決,哈哈。。
]]>
今后要多寫寫blog,記錄工作、學習中的問題和經驗。也算是加強文檔能力的一種途徑吧!
有空也要把博客園的東西遷過來,畢竟那邊是.net為主的。
]]>