#
今天到中山電視臺,但根本沒與用戶深入交流的機會。
如果真是做HFC網絡的監測,那我們肯定不行,只能放棄。
不過聽他的意思,又好像是要做一般IP網絡監測,那我們還有機會。
用TreeMap裝載snmp的ifTable,真是個不錯的選擇
優點:能排序,又有hashMap的功能。
唯一的不好就是只能按主鍵排序
public class IfEntityTable extends TreeMap<String,IfEntity>
{
private static final long serialVersionUID = 25611283245733824L;
public void add(IfEntity ifObj)
{
put(ifObj.getIndex(),ifObj);
}
}
public class IfEntity implements TableItem
{
//------------property----------
private String index;
private String descr;
}
SourceView綜合監控管理系統總體設計如下:
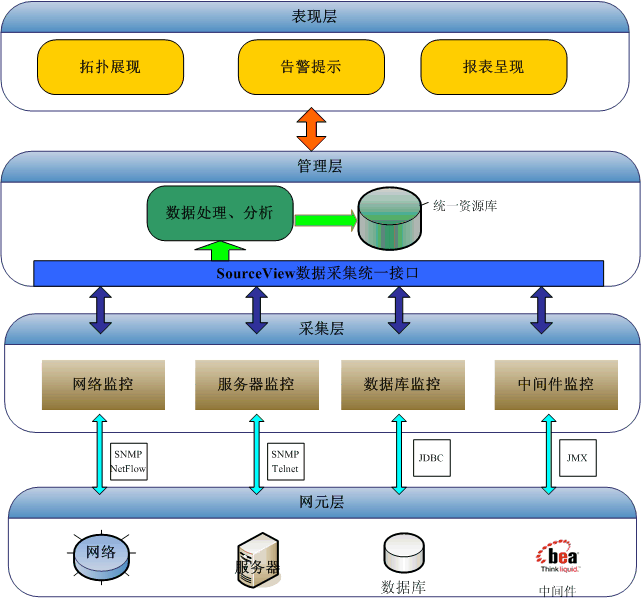
底層實現數據采集,系統通過多種方式對網絡設備、服務器、數據庫系統以及中間件進行數據采集。采集方式主要有SNMP、NetFlow、SysLog、SNMPTrap、Telnet、JDBC和JMX。
中間層負責數據處理和分析,包括系統的主要功能,實現了IT系統靜態數據和動態數據的整合;并實現配置管理、事件管理、故障管理、性能管理等。這一層次中主要實現數據的集中分析和關聯分析,將各個監控對象的故障數據和性能數據進行集中整合。
上層是綜合監控管理系統的表現層,這一層主要包含拓撲視圖、性能報表和故障提示等。用戶可以通過web的方式,以圖形的方式查詢設備的運行情況,可以分為實時和歷史兩種模式;對于設備運行過程中出現的故障能夠在圖形上展現出來,并且按照用戶設定的方式進行告警。
以前畫這個總體結構圖都是copy別人的,但其實沒有一個能真正反映我的設計思想,
所以今天專門花了好長時間用visio畫了個自己的結構圖。
根據用戶需求,XX公安綜合監控管理系統項目的建設目標如下:
?1.建立面向運維業務需要的自動化監控管理體系,提高管理質量。
?2.保證系統可靠性和可用性,為用戶提供7×24小時不間斷的可靠服務。
?3.在復雜的異構環境中實現集中統一管理,輕松維護復雜的異構環境并使之有效運行。
?4.把運維人員從管理產品的復雜負擔中解放出來,系統能實現自動的檢測和告警。
?5.將錯綜復雜的系統信息,各類系統事件按照運行管理的需求進行過濾整理,幫助系統維護人員專注于重要事件的管理和響應。
6.總結出對系統管理、業務管理、服務管理有用的信息,為管理者提供更全面,更直接的管理信息,為制訂相關決策提供依據。
系統設計原則:
1.標準化原則:遵循TCP/IP、SNMP和NetFlow等相關的國際標準或工業標準,支持對設備廠商通用MIB的管理;
2.開放性原則:支持對各種網絡設備廠商管理工具的集成,具有開放的API接口,支持對網管系統的二次開發;
3.易用性原則:要求管理功能以良好直觀的界面和圖形方式實現,能通過瀏覽器方式進入系統;
4.健壯性原則:系統監控的設備多,數據量巨大,系統本身應健壯、易于維護;
5.節省資源原則:系統設計在滿足用戶需求的基礎上,應盡量減少對網絡帶寬及系統資源的占用。
今天對XX公安進行需求調研。根據調研,XX公安主要有以下四個方面需求:
1. 網絡
(1)XX公安的網絡拓撲為星加環結構,其中星形結構作備份用。如果網絡拓撲從環形變為星形,系統必須給出告警。
(2)對于匯接層的路由設備,如果其路由表發生變化,系統應給出告警。
(3)對于匯接層的路由設備,可以開啟netflow協議,網管系統捕獲netflow數據包,以分析網絡流量以及帶寬利用率,對于異常流量,系統應給出告警。
2. 服務器
XX公安服務器安裝有多種操作系統,其中包括Windows2003、AIX、Hp-Ux和Fedora Linux。
對于這些服務器,主要監控:
服務器基本性能指標;
服務器進程;
服務器的錯誤日志;
3. 數據庫
XX公安現有的數據庫系統包括Oracle8i、Oracle9i、Oracle10g和MS SQL-Server2000。
對于這些數據庫系統,主要監控:
數據庫基本性能指標;
數據庫錯誤日志。
4. 中間件
XX公安現有的中間件系統包括WebLogic8.0和WebSphere5.0,主要監控中
間件中數據庫連接池當前工作狀況。
Architecture Reconstruction
Intended vs. realized architecture. Evaluation of an architecture's properties is critical to successful system development. However, reasoning about a system's intended architecture must be recognized as distinct from reasoning about its realized architecture. As design and eventually implementation of an architecture proceed, faithfulness to the assumptions of the intended architecture is not always achieved. This is particularly true in cases where the intended architecture is not completely specified, documented or disseminated to all of the project members. This problem is exacerbated during maintenance and evolutionary development, as architectural drift and erosion occur.
Why architecture reconstruction important. To apply reasoning about the properties of a system's intended architecture to the properties of the implemented system, we must either ensure that the realized architecture conforms to the intended architecture or change the intended architecture to match reality. Both cases may require reconstructing the architecture of the realized system.
Phases of reconstruction. Architecture reconstruction is an iterative and interactive process, comprising four phases.
- The first phase is the extraction, from implementation artifacts (including source code and dynamic information such as event traces), of a set of extracted views that represent the system's fundamental structural and behavioral elements.
- The second phase is fusion of the extracted views to create fused views that augment or improve the extracted views.
- During the third phase, the analyst iteratively and interactively develops and applies patterns to the fused views to reconstruct architecture-level derived views. Patterns provide the medium for an analyst to express their understanding of a system's architecture as structural and attribute-based relationships among its components.
- Finally, the derived views may be explored for the purposes of evaluating architectural conformance, identifying targets for reengineering or reuse and analyzing the architecture's qualities.
The reconstruction process can be most effectively supported by the integration of existing tools and techniques. There currently exist a large number of commercial and research tools that provide the basic mechanisms for view extraction. Similarly, there are several tools and techniques available for performing view fusion and reconstruction. The synthesis of these tools and techniques provides a support environment for software architects and analysts reconstructing architectures.
To compliment our previous work in reconstruction we are currently surveying tools that are available for reconstruction to determine the current state of the practice for reconstructing architectural representations. We will study the information that these tools extract with emphasis on how they present the extracted views and how they aid in analysis of legacy systems.
The SEI will assist organizations with architecture reconstruction exercises.
Methods for Software Architecture Design
Software architecture forms the backbone for any successful software-intensive system. An architecture is the primary carrier of a software system's quality attributes such as performance or reliability. Designing the right architecture is the linchpin for software project success. Designing the wrong one is a recipe for guaranteed disaster.
Methods for Software Architecture Evaluation
How do you know if a software architecture for a system is suitable without having to build the system first?
The answer is to conduct an evaluation of it. A formal software architecture evaluation should be a standard part of the architecture-based software development life cycle. Architecture evaluation is a cost-effective way of mitigating the substantial risks associated with this highly important artifact.
The achievement of a software system's qualities attributes depends much more on the software architecture than on code-related issues such as language choice, fine-grained design, algorithms, data structures, testing, and so forth. Most complex software systems are required to be modifiable and have good performance. They may also need to be secure, interoperable, portable, and reliable. But for any particular system, what precisely do these quality attributes - modifiability, security, performance, reliability - mean? Can a system be analyzed to determine these desired qualities? How soon can such an analysis occur? What happens these quality attributes are in conflict with each other? How can the tradeoffs be examined, analyzed, and captured?
Methods for Software Architecture Documentation
Because architectures are intellectual constructs of enduring and long-lived importance, communicating an architecture to its stakeholders becomes as important a job as creating it in the first place. If the architecture cannot be understood so that others can build systems from it, analyze it, maintain it, and learn from it, then the effort put into crafting it will by and large have been wasted.
Documenting a software architecture is a matter of choosing a set of relevant views of the architecture, documenting each of those views, and then documenting information that applies to more than one view or to the set of views as a whole.
琢磨了一個多星期,終于把netflow做出來了。
關鍵在于理解Cisco netflow v9白皮書《Cisco IOS NetFlow Version 9 Flow-Record Format》。
我想要的就是得到源IP、目標IP、源端口、目標端口以及使用的協議,
這是程序運行的結果:
Router IP=192.168.0.254
收到netflow包,包長=1420
version=9
count=29
unixSecs=2007-11-23 03:15:19
packageSequence=9329
源IP=59.41.62.50
目標IP=192.168.3.90
協議=6
源Port=7709
目標Port=2620
源IP=58.251.60.66
目標IP=58.253.18.208
協議=6
源Port=12000
目標Port=1469
源IP=192.168.2.20
目標IP=58.61.32.11
協議=17
源Port=4000
目標Port=8000
源IP=202.106.46.151
目標IP=58.253.18.208
協議=17
源Port=53
目標Port=1034
源IP=192.168.2.20
目標IP=219.133.60.243
協議=17
源Port=4000
目標Port=8000
源IP=219.133.60.153
目標IP=58.253.18.208
協議=17
源Port=8000
目標Port=1035
源IP=192.168.3.90
目標IP=61.152.112.125
協議=6
源Port=2633
目標Port=80
-------------------------/192.168.0.254
收到netflow包,包長=1424
version=9
count=29
unixSecs=2007-11-23 03:16:12
packageSequence=9354
源IP=58.251.60.182
目標IP=192.168.2.154
協議=6
源Port=80
目標Port=2244
源IP=219.133.49.75
目標IP=58.253.18.208
協議=17
源Port=8000
目標Port=2851
源IP=192.168.2.156
目標IP=219.133.49.75
協議=6
源Port=2851
目標Port=80
源IP=4.2.2.4
目標IP=58.253.18.208
協議=17
源Port=53
目標Port=2166
源IP=192.168.2.156
目標IP=222.141.220.165
協議=6
源Port=2981
目標Port=80
下一步就是把結果入庫,然后分析,得出用戶想要的東西。
1. 設備管理中->查尋,要支持模糊查尋。
2. 拓撲圖中可以無限滾動,不好。
3. 報警數據應該立即插入數據庫,才能在告警平臺上顯示。
4. 報表上設備太多,沒有查找功能。
5. 生成的excel報表中,沒有設備名稱以及查詢時間
6. 修改了告警平臺,壓縮告警,以及刪除告警(同時刪除多條相同的記錄)
7. 去掉Cisco的電源和風扇監視器(因為沒什么用,而且耗資源)。
8. 要動態更新接口數據。
9. 如果ping不通,其它監視器則不運行。
10. 網絡拓撲太大,應該按子網來分。
這些意見對我們系統改進很有幫助,將在2.0中一一改進。
In order to make a analysis of business applications,we decide to
add netflow feature into SourceView2.0.
NetFlow, much like RMON-based probes, can give you information on where,
why, how and by whom specific applications are being used and how the usage
might affect the network. NetFlow is a part of Cisco’s IOS software, and the current
version, 9, is currently moving toward standardization in the IETF as IPFIX.
Networking vendors other than Cisco, such as Enterasys and Juniper, are taking a
role in shaping the standard, and are already showing interest in adopting IPFIX.
This, of course, makes NetFlow/IPFIX far more attractive as a consistent source
for information about application flows over a network in heterogeneous environments.
NetFlow provides the following information:
* IP address source (who is sending an application service?)
* IP address destination (who is receiving service?)
* Source port (what application is it?)
* Destination port (what application is it?)
* Layer 3 protocol type
* Class of service
以前對SNMP Trap沒有真正理解,今天收集到了Lucent ATM trap信息,
突然間有了收獲,明白了兩點:
1. 以前看過的Trap都是公用的。而設備產商可自定義Trap,比如Lucent
ATM發出來的Trap就全是自定義的。generic=6(enterpriseSpecific)表示這
個Trap是自定義的。
2. 這些Trap中的oid其實在acmib.mib中都有定義,查acmib就可以知道這
個trap是什么意思。所以,只要能把解析acmib,把acmib中symbol和oid都導
入數據庫中,便可根據oid來查詢symbol,從而知道這個trap的意思。
snmp trap from=172.16.1.36
generic=6
specific=5
oid=1.3.6.1.4.1.1751.2.18.8.3
version=V1TRAP
1.3.6.1.4.1.1751.2.18.15.2.0 = 905004
1.3.6.1.4.1.1751.2.18.15.3.0 = 12
1.3.6.1.4.1.1751.2.18.2.23.1.2.0 = 2

“NetworkMapper 是由本公司和清華大學聯合研制的以太網絡管理產品。系統采用具有自主知識產權的在國際上處于領先位置的核心技術”,不知有啥核心技術?
拓撲發現還可以,但其他基本沒什么亮點,而且這個界面很久以前肯定看過,只是記不得是哪個產品了,呵呵。
很久以前一個網管給我的一個軟件,系統為c/s程序。它的技術支持http://www.alliedtelesis.com.cn/support.htm已經不能訪問了,呵呵。
最大的優點就是發現得比較全面,而且操作比較方便,在拓撲圖上基本可以找到你想要的所有操作。
還有,可查看的內容也很豐富。